Lab: traps
This lab explores how system calls are implemented using traps.
You will first do a warm-up exercises with stacks and then you will
implement an example of user-level trap handling.
Before you begin the traps lab, read Chapter 4 of the xv6 book, and
related source files:
- kernel/trampoline.S: the assembly involved in
changing from user space to kernel space and back
- kernel/trap.c: code handling all interrupts
In this lab, there are several questions for you to answer. Questions are in boxes with a light orange background.
Write each question and its answer in your notebook. You will state the percentage of questions answered on your lab submission.
The Linux grep command can be helpful on some questions. For example, suppose a question asks you about the macro TRAPFRAME. You can discover the definition and uses of the macro TRAPFRAME by issuing the following Linux grep command in the kernel directory.
$ grep TRAPFRAME *.h
memlayout.h:// TRAPFRAME (p->trapframe, used by the trampoline)
memlayout.h:#define TRAPFRAME (TRAMPOLINE - PGSIZE)
memlayout.h:#define USYSCALL (TRAPFRAME - PGSIZE)
% grep TRAPFRAME *.c
proc.c: if(mappages(pagetable, TRAPFRAME, PGSIZE,
proc.c: uvmunmap(pagetable, TRAPFRAME, 1, 0);
proc.c: uvmunmap(pagetable, TRAPFRAME, 1, 0);
To start the lab, switch to the trap branch:
$ git fetch
$ git checkout traps
$ make clean
Problem 1: RISC-V assembly
It will be important to understand a bit of
RISC-V assembly. You were exposed to ARM assembly in CPSC 305.
RISC-V and ARM are both Reduced Instruction Set Computers (RISC).
Recall that attributes of RISC architectures are
- Load/store architecture. All memory is accessed with loads (move memory to registers)
and stores (more registers to memory). Arithmetic and logic instructions operate on registers.
- Many registers.
- All instructions are the same size. Both RISC-V and ARM have 32-bit instructions.
- Single clock simple instructions.
- Easier to pipeline.
Moving from ARM to RISC-V is rather straightforward especially since we do not have
to become expert assembly programmers for the course.
There is a file
user/call.c in your xv6 repo. make fs.img compiles it
and also produces a readable assembly version of the program in
user/call.asm.
The C code for user/call.c is the following.
int g(int x) {
return x+3;
}
int f(int x) {
return g(x);
}
void main(void) {
printf("%d %d\n", f(8)+1, 13);
exit(0);
}
Read the code in call.asm for the functions g, f, and main.
The instruction
manual for RISC-V is on the reference page, if you need it.
Answer the following questions in notebook.
1. Which registers contain arguments to functions? For example, which
register holds 13 in main's call to printf?
2. Where is the call to function f
in the assembly code for main? Where is the call to g? (Hint: the
compiler may inline functions.)
3. At what address is the
function printf located?
4. What value is in the register ra
just after the jalr to printf in main?
5. Run the following code on Xv6.
You will have to create a user program and add it to UPROGS in the Makefile.
Include the running of your program in your lab-traps-handin.txt.
unsigned int i = 0x00646c72;
printf("H%x Wo%s", 57616, &i);
What is the output?
Here's an ASCII
table that maps bytes to characters.
The output depends on that fact that the RISC-V is
little-endian. If the RISC-V were instead big-endian what would
you set i to in order to yield the same output?
Would you need to change
57616 to a different value?
Here's
a description of little- and big-endian
and
a more
whimsical description.
6. What are the attributes of a RISC architecture?
7. Compare a RISC architecture to a CISC architecture?
Problem 2: Backtrace
For debugging it is often useful to have a backtrace: a list
of the function calls on the stack above the point
at which the error occurred.
To help with backtraces, the compiler generates machine code that maintains a stack
frame on the stack corresponding to each function in the
current call chain. Each stack frame contains of the return
address, "saved frame pointer", saved registers, and local variables.
The "saved frame pointer" points to the caller's stack frame, which has a
"saved frame pointer" that points to its caller's stack frame. Register
s0 contains a pointer to the current stack frame
(it actually points to the the address of the saved return address
on the stack plus 8). Your backtrace
should begin with the value in s0, walk up the stack, and print the
saved return address (ra) in each stack frame.
Implement a backtrace() function
in kernel/printf.c. Insert a call to this function
in sys_sleep, and then run bttest, which
calls sys_sleep.
You will have to add a backtrace function prototype in defs.h.
Your output should be a list of return addresses with this form (but the numbers will likely be different):
$ bttest
0x00000000800021f2
0x0000000080002064
0x0000000080001d26
The Linux program
addr2line translates an address to a filename and line number using a file that has debug information in it. The file
kernel/kernel has the Xv6 kernel's executable and debug information.
addr2line reads addresses as input from standard input until you enter Ctrl-D.
You can enter addresses one at a time, or copy/paste all three.
After bttest exit qemu. In a terminal window:
run riscv64-linux-gnu-addr2line -e kernel/kernel (or riscv64-unknown-elf-addr2line -e kernel/kernel) and cut-and-paste the addresses from your backtrace, entering one address at a time, like this:
$ riscv64-linux-gnu-addr2line -e kernel/kernel
0x00000000800021f2
/home/faculty/ecooper/gustyx/kernel/sysproc.c:71
0x0000000080002064
/home/faculty/ecooper/gustyx/kernel/syscall.c:145
0x0000000080001d26
/home/faculty/ecooper/gustyx/kernel/trap.c:76
Or you can copy/paste all three like this:
$ riscv64-linux-gnu-addr2line -e kernel/kernel
0x00000000800021f2
0x0000000080002064
0x0000000080001d26
Ctrl-D
You should see something like this:
kernel/sysproc.c:71
kernel/syscall.c:145
kernel/trap.c:67
Some Hints
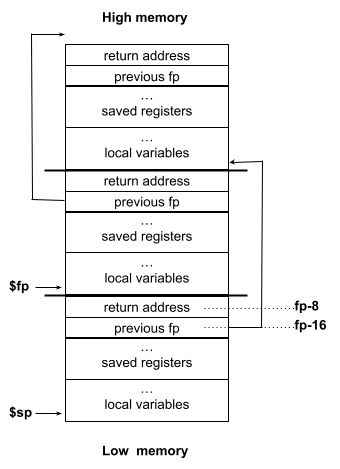
- The following diagram shows a layout of stack frames.
Note that the return address lives at a fixed offset (-8) from the frame pointer of a
stackframe, and that the saved frame pointer lives at fixed offset (-16) from the frame pointer.
- Recall that a stack frame grows from high memory to low memory. Everytime a function
is called, the function entry sequence allocates the stack by subtracting from the stack pointer
to allocate enough space for (1) local variables, (2) any registers the function will overwrite,
(3) the previous (saved) frame pointer, and (4) the return address.
- When the function returns, the stack frame is deallocated.
- Consider the function entry sequence for a simple add function with prototype:
int add(int a, int b).
add:
# prologue or entry sequence
addi sp,sp,-32 # allocate 32 byte stack
sd ra,24(sp) # put ra on stack
sd s0,16(sp) # put previous fp on stack
addi s0,sp,32 # create current fp
mv a5,a0 # param a is in a0
mv a4,a1 # param b is in a1
sw a5,-20(s0) # put a on stack
mv a5,a4 # put b into a5
sw a5,-24(s0) # put b on stack
-----------------------------------------
# function body
lw a5,-20(s0) # get a from stack
mv a4,a5
lw a5,-24(s0)
... more code ...
-----------------------------------------
# epilogue or exit sequence
mv a0,a5 # put return value in a0
ld ra,24(sp) # get ra from stack
ld s0,16(sp) # reset previous fp
addi sp,sp,32 # deallocate stack
jr ra # return
8. Which of the instructions allocates the stack?
9. What is the size (in bytes) of the allocated stack?
10. Why must the return address be saved on the stack?
To answer this question, think of a scenario where you cannot use the ra register without saving and restoring it.
11. Which of the instructions deallocates the stack?
12. The parameters a and b for the above function add are stored on the stack.
What is the offset of a relative to the frame pointer?
What is the offset of a relative to the stack pointer?
- The GCC compiler stores the frame pointer of the currently
executing function in the
register s0. Add the following function
to kernel/riscv.h:
static inline uint64
r_fp()
{
uint64 x;
asm volatile("mv %0, s0" : "=r" (x) );
return x;
}
and call this function in backtrace to read the current frame pointer. r_fp() uses in-line
assembly to read s0.
After reading s0, r_fp() returns its value.
13. The function r_fp() is a C function, but it contains assembly code. How does the C programming
language allow this?
14. What is the purpose of the volatile keyword?
- Your backtrace function can call r_fp() as follows.
uint64 fp = r_fp();
The variable fp contains a 64-bit address which points to the current stack frame.
Using C pointers, you can access the return address and the previous frame pointer as follows.
uint64 ra = *(uint64*)(fp - 8);
uint64 pfp = *(uint64*)(fp - 16);
- Your backtrace() will need a way to recognize that
it has seen the last stack frame, and should stop.
A useful fact is that the memory allocated for each kernel
stack consists of a single page-aligned page,
so that all the stack frames for a given stack
are on the same page.
You can use
PGROUNDDOWN(fp)
(see kernel/riscv.h) to identify the
page that a frame pointer refers to.
The following shows initializing a frame pointer variable, and a while loop that terminates.
uint64 fp = r_fp();
while(fp != PGROUNDDOWN(fp)){
...
}
- Add the prototype for your backtrace() to kernel/defs.h so that
you can call backtrace in sys_sleep.
Add this prototype in the section of the file for printf.c.
// printf.c
void backtrace(void); ← Add this line
void printf(char*, ...);
void panic(char*) __attribute__((noreturn));
void printfinit(void);
- Implement your backtrace() function
in kernel/printf.c.
The following is my implementation of the backtrace() function,
which you place in kernel/printf.c.
You will notice that I print more than the return address as described in the
required specification blue box.
void
backtrace()
{
uint64 fp = r_fp();
while(fp != PGROUNDDOWN(fp)){
printf("ra: %p\n", *(uint64*)(fp - 8));
printf("fp: %p\n", fp);
printf("PGR(fp): %p\n", PGROUNDDOWN(fp));
fp = *(uint64*)(fp - 16);
printf("pfp: %p\n", fp);
printf("PGR(pfp): %p\n", PGROUNDDOWN(fp));
}
}
- Insert a call to your backtrace()
in sys_sleep, which is in the file sys_proc.c.
uint64
sys_sleep(void)
{
int n;
uint ticks0;
argint(0, &n);
if(n < 0)
n = 0;
acquire(&tickslock);
ticks0 = ticks;
while(ticks - ticks0 < n){
if(killed(myproc())){
release(&tickslock);
return -1;
}
sleep(&ticks, &tickslock);
}
release(&tickslock);
backtrace(); ← Add this line
return 0;
}
Testing
We have provide the user program bttest.c that you may run to test your implementation of backtrace(). The test is really simple, shown as follows.
int
main(int argc, char *argv[])
{
sleep(1);
exit(0);
}
Since you have inserted a call to backtrace() in sys_sleep(), this
test will show you the results of a backtrace.
The following a sample output.
xv6 kernel is booting
hart 1 starting
hart 2 starting
init: starting sh
$ bttest
0x0000000080003324
0x0000000080003162
0x0000000080002e22
$
ecooper@cpsc:~/xv6demo$ riscv64-linux-gnu-addr2line -e kernel/kernel
0x0000000080003324
/home/faculty/ecooper/xv6demo/kernel/sysproc.c:72
0x0000000080003162
/home/faculty/ecooper/xv6demo/kernel/syscall.c:200
0x0000000080002e22
/home/faculty/ecooper/xv6demo/kernel/trap.c:76
ecooper@cpsc:~/xv6demo$
Note that we placed the call to trace() in sys_sleep(), which is a system call. The function trace goes from usertrap() to syscall() to sys_sleep() to backtrace().
- The trap.c:76 line above is where usertrap() calls syscall().
- The syscall.c:200 line above is where syscall() actually calls sys_sleep()
- The sysproc.c:72 line above is where sys_sleep() calls backtrace().
Once your backtrace is working, you can call it from panic
in kernel/printf.c so that you see the kernel's backtrace
when it panics. This is a new programming tool.
Problem 3: Alarm
You do not have to implement this solution, but you must answer the questions.
In this exercise you'll add a feature to xv6 that periodically alerts
a process as it uses CPU time. This might be useful for compute-bound
processes that want to limit how much CPU time they chew up, or for
processes that want to compute but also want to take some periodic
action. More generally, you'll be implementing a primitive form of
user-level interrupt/fault handlers; you could use something similar
to handle page faults in the application, for example.
You should add two new system calls: (1) sigalarm(interval, handler) system call.
and (2) sigreturn() system call.
If an application calls sigalarm(n, fn), then after every
n "ticks" of CPU time that the program consumes, the kernel
should cause application function
fn() to be called. When fn() calls sigreturn(), the application
should resume where it left off. The last statement in the function fn() will
be a call to sigreturn().
A tick is a fairly arbitrary unit of
time in xv6, determined by how often a hardware timer generates
interrupts.
If an application calls sigalarm(0, 0), the kernel should
stop generating periodic alarm calls.
System Calls Implementation
The following shows my implementation of the two system calls, which I placed at the bottom of sysproc.c. Of course, you would have to implement them as system calls by following the steps
at Reference: Xv6 System Calls.
uint64
sys_sigalarm(void)
{
struct proc* p = myproc();
argint(0, &p->interval);
argaddr(1, &p->handler);
p->regs = p->trapframe + sizeof(struct trapframe);
return 0;
}
uint64
sys_sigreturn(void){
struct proc* p = myproc();
memmove(p->trapframe, p->regs, sizeof(struct trapframe));
p->ticks = 0;
return p->trapframe->a0;
}
usertrap() Implementation
In addition to the two system calls, you have to update usertrap() (located in
kernel/trap.c to call the function establised to handle the alarm.
The following shows my updates to usertrap()
void
usertrap(void)
{
int which_dev = 0;
... some code is not shown ...
struct proc *p = myproc(); ← Line 1
// save user program counter. ← Line 2
p->trapframe->epc = r_sepc(); ← Line 3
... some code is not shown ...
// give up the CPU if this is a timer interrupt.
if(which_dev == 2) {
if(p->interval != 0){
p->ticks++;
if(p->ticks == p->interval){
memmove(p->regs, p->trapframe, sizeof(struct trapframe));
p->trapframe->epc = p->handler;
}
}
yield();
}
usertrapret();
}
The value p->trapframe->epc contains return address when returning from a trap.
You can observe how it is established by reading code marked with arrows and labeled
Line 1, Line 2, and Line 3. The struct proc *p points the the process that was
interrupted. When this happens, the register sepc receives the address of the
instruction when the interrupt occurred. In the normal scenario, you return to this address
when finished processing the interrupt. However, in this case, we change the return value to be
the address of the handler function established by calling sigalarm() function.
Thus, when we return from this timer interrupt, we will return to the handler. The handler will call
sigreturn() when done, which will return to the original function interrupted by the timer interrupt. It accomplishes this because the registers at the time of the interrupt were saved
and then restored by sigreturn().
15. Describe the three members added to the struct proc that are used by
this implementation of the sigalarm and sigreturn system calls.
alarmtest.c
You'll find a file user/alarmtest.c in your xv6
repository. Add it to the Makefile. It won't compile correctly
until you've added sigalarm and sigreturn
system calls (see below).
alarmtest calls sigalarm(2, periodic)
in test0 to ask the kernel to force a call
to periodic() every 2 ticks, and then spins for a while. You
can see the assembly code for alarmtest in user/alarmtest.asm, which
may be handy for debugging.
void
periodic()
{
count = count + 1;
printf("alarm!\n");
sigreturn();
}
void
test0()
{
int i;
printf("test0 start\n");
count = 0;
sigalarm(2, periodic);
for(i = 0; i < 1000*500000; i++){
if((i % 1000000) == 0)
write(2, ".", 1);
if(count > 0)
break;
}
sigalarm(0, 0);
if(count > 0){
printf("test0 passed\n");
} else {
printf("\ntest0 failed: the kernel never called the alarm handler\n");
}
}
Your solution is correct when
alarmtest produces output like this.
$ alarmtest
test0 start
........alarm!
test0 passed
test1 start
...alarm!
..alarm!
...alarm!
..alarm!
...alarm!
..alarm!
...alarm!
..alarm!
...alarm!
..alarm!
test1 passed
test2 start
................alarm!
test2 passed
test3 start
test3 passed
$
16. The
test0() in
alarmtest.c is given by the following with line numbers.
1 void periodic() {
2 count = count + 1;
3 printf("alarm!\n");
4 sigreturn();
5 }
6
7 void test0() {
8 int i;
9 printf("test0 start\n");
10 count = 0;
11 sigalarm(2, periodic);
12 for(i = 0; i < 1000*500000; i++){
13 if((i % 1000000) == 0)
14 write(2, ".", 1);
15 if(count > 0)
17 break;
18 }
19 sigalarm(0, 0);
20 if(count > 0){
21 printf("test0 passed\n");
22 } else {
23 printf("\ntest0 failed: the kernel never called the alarm handler\n");
24 }
25 }
A. What does line 11 do?
B. What happens during the loop on lines 12 through 18?
C. What does line 4 do?
D. What does line 19 do?
When you're done, your solution will be only a few lines of code,
but it may be tricky to get it right. We'll test your code with the
version of alarmtest.c in the original repository. You can modify
alarmtest.c to help you debug, but make sure the original alarmtest
says that all the tests pass.
Some Hints
- Since sigalarm and sigreturn are system calls,
you can reviews to steps for adding system calls at
Reference: Xv6 System Calls.
- Your solution will require you to save and restore
registers---what registers do you need to save and restore to resume
the interrupted code correctly? (Hint: it will be many).
- Have usertrap save enough state in
struct proc when the timer goes off
that sigreturn can correctly return to the
interrupted user code.
- Prevent re-entrant calls to the handler----if a handler hasn't
returned yet, the kernel shouldn't call it again. test2
tests this.
- Make sure to restore a0. sigreturn is a system call,
and its return value is stored in a0.
17. The current code in
usertrap() for a timer interrupt is the following.
// give up the CPU if this is a timer interrupt.
if(which_dev == 2)
yield();
Design the algorithm that will call the signal handler when the selected number of ticks has expired.
This requires some thought. You must examine the struct proc member ticks to see if
it equal to the interval. If it is, what do you do? You do not call a function, because this is a
timer interrupt. How do you manipulate the trap frame such that the sigalarm() handler is called?
If you study the remainder of this problem specification, you will get lots of clues as to how to design this.
Step 1: invoke handler
You want to first make sure the kernel can successfully jump to the
alarm handler in user space. Modify the kernel to have a working sigalarm and
a simplified sigreturn You can use test0 of alarmtest
to test your changes. The alarm handler is test0 will print alarm!
when it is called.
Don't worry yet
what happens after the "alarm!" output; it's OK for now if your
program crashes after printing "alarm!". At this point, you just want the kernel
to call the alarm handler. Here are some hints:
- test0 of alarmtest calls sigalarm to see if its
alarm handler is properly called. You can examine test0 to see the
the details of the following, which is a mixture of code and psuedo code.
volatile static int count;
void periodic() { // test0 alarm handler
count = count + 1;
printf("alarm!\n");
sigreturn();
}
void test0() {
count = 0;
sigalarm(2, periodic);
loop long enough for 2 ticks {
if (count > 0)
break;
}
sigalarm(0, 0); // turn off alarms
if (count > 0)
printf("test0 passed\n");
}
- You must to modify the Makefile to cause alarmtest.c
to be compiled as an xv6 user program. Recall this is done by adding
$U/_alarmtest\ to UPROGS.
- You must put the function prototypes for sigalarm and sigreturn
in user/user.h.
int sigalarm(int ticks, void (*handler)());
int sigreturn(void);
- You must update user/usys.pl (which generates user/usys.S),
kernel/syscall.h, and kernel/syscall.c
to allow alarmtest to invoke the sigalarm and
sigreturn system calls. Please review
Reference: Xv6 System Calls
if you need a refresher on adding system calls to Xv6.
- For now, your sys_sigreturn should just return zero.
- Your sys_sigalarm() should store the alarm interval and
the pointer to the handler function in new fields in the proc
structure (in kernel/proc.h). These fields can be
int interval; // alarm interval
uint64 handler; // pointer to the handler function
- You'll need to keep track of how many ticks have passed since the
last call (or are left until the next call) to a process's alarm
handler; you'll need a new field in struct proc for this
too. This field can be
int ticks; // ticks have passed since the last call
- You can initialize the new proc fields to 0 in allocproc()
in proc.c.
- Every tick, the hardware clock forces an interrupt, which is handled
in usertrap() in kernel/trap.c. This is where you will update
the field ticks.
- The function usertrap() is called for timer interrupts and
device interrupts. The variable which_dev indicates the interrupt type.
which_dev is a 2 for timer interrupts.
You only want to manipulate a process's alarm ticks if there's a
timer interrupt; you want something like
if(which_dev == 2) ...
- Only invoke the alarm function if the process has a
timer outstanding. Note that the address of the user's alarm
function might be 0 (e.g., in user/alarmtest.asm, periodic is at
address 0). This means you cannot us a nonzero compare on the proc
field handler to determine if the the process has a timer
outstanding. You must use a nonzero compare to the field interval
to determine if the process has a timer outstanding.
- You'll need to modify
usertrap() so that when a
process's alarm interval expires, the user process executes
the handler function.
- The trapframe contains the user space return address in the field epc.
When a trap occurs the PC value that was interrupted in placed in the sepc register.
In the case of a system call, the value in sepc is the addres of the ecall
instruction. When returning to user space following a system call, the kernel must
return to sepc+4. usertrap() has code that accomplishes the following.
p->trapframe->epc = r_sepc() + 4;
r_sepc() is in riscv.h, and it has an assembly macro that reads to
sepc register. At the beginning of this lab, you added r_fp() to
riskv.h to read the frame pointer.
18. The actual code in usertrap() is different than the above line that adds 4 to
r_sepc().
How does the usertrap() code accomplish adding 4 to the sepc register?
- In the case where a timer interrupt must return to the process' handler, you must put
the handler's address in p->trapframe->epc. The pseudo code in usertrap
looks like the following. Then instead of returning to the instruction after the
system call, the return is to the process' handler.
if (this is a timer interrupt) {
if (this proc has a handler) {
increment ticks
if (tick == interval)
p->trapframe->epc = p->handler
}
19. How does usertrap() determine if the trap is a syscall?
- It will be easier to look at traps with gdb if you tell qemu to
use only one CPU, which you can do by running
make CPUS=1 qemu-gdb
- You've succeeded if alarmtest prints "alarm!".
20. Several parts to this question.
A. What code executes initially when a trap/interrupt occurs?
B. What mode is the CPU in when it executes the trap handling code?
C. What page table is used when a trap/interrupt initially occurs?
D. What does the sfence RISC-V instruction do, and where is it used in the trap processing?
test1/test2()/test3(): resume interrupted code
- Chances are that alarmtest crashes in test0 or test1 after it prints
"alarm!", or that alarmtest (eventually) prints "test1 failed",
or that alarmtest exits without printing "test1 passed".
To fix this, you must
ensure that, when the alarm handler is done,
control returns to
the instruction at which the user program was originally
interrupted by the timer interrupt. You must ensure that
the register contents are restored to the values they held
at the time of the interrupt, so that the user program
can continue undisturbed after the alarm.
Finally,
you should "re-arm" the alarm counter after each time it goes
off, so that the handler is called periodically.
- As a starting point, we've made a design decision for you:
user alarm handlers are required to call the sigreturn
system call when they have finished. Have a look at
periodic in alarmtest.c for an example.
This means that you can add code to usertrap and
sys_sigreturn that cooperate to cause the user
process to resume properly after it has handled the alarm.
Once you pass test0, test1, test2, and test3
run usertests -q to make sure you didn't break any other parts
of the kernel.
user/usertests.c performs comprehensive testing of all of the Xv6 provided user programs. When you have created a system that is to be updated, you should create a collection of tests that can be run whenever you update the system. This allows you to make sure that you updates did not break any code in the original system. user/usertests.c is the collection of tests for the Xv6 provided user programs, and usertests.c provides a quick version of the tests by using the -q option. Be aware that the -q option is still rather slow on our CPSC server.
Submit the lab
This completes the lab.
Read Lab Submissions for instructions on how
to submit your lab.
